THE 7AI PLATFORM
AI Agents That Actually Do The Work
Autonomous AI agents that investigate security alerts, form conclusions, and take action—transforming security operations from hours to minutes.

What makes 7AI different
AI Agents
PROVEN IN PRODUCTION
7AI agents aren't chatbots or copilots waiting for instructions. They're autonomous specialists that investigate alerts, correlate data across your environment, form conclusions, and take action— just like your best analysts, at machine speed.
-
Purpose-built
Each agent is an expert at specific security tasks
-
Context Aware
Full enterprise context—not isolated alert analysis
-
Architecturally grounded
Bounded by design to eliminate hallucinations
-
Autonomous
Make decisions, adapt, and complete their mission
Platform capabilities
The Complete Security Operations Stack
From ingestion to response, 7AI handles the full lifecycle of security operations—with AI agents at every layer.
CASES
Unified incident management that brings together investigations, evidence, and team collaboration in one place.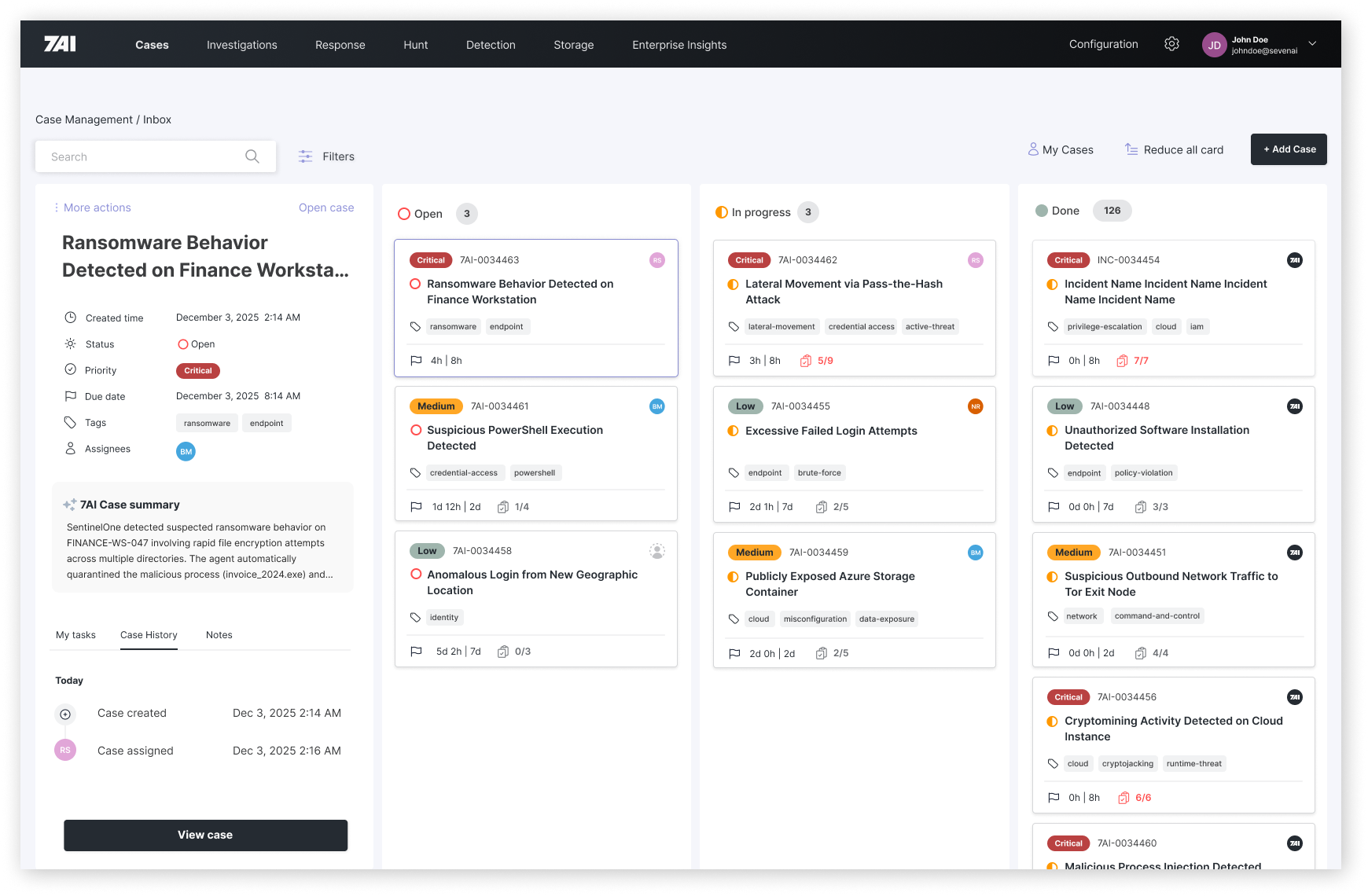
What it Does
Cases provide a single source of truth for every security incident. AI agents automatically populate cases with investigation findings, correlate related alerts, and maintain a complete audit trail—giving analysts full context without the manual grunt work.
- Auto-populated investigation summaries
- Cross-alert correlation
- Evidence collection & chain of custody
- Team collaboration & handoffs
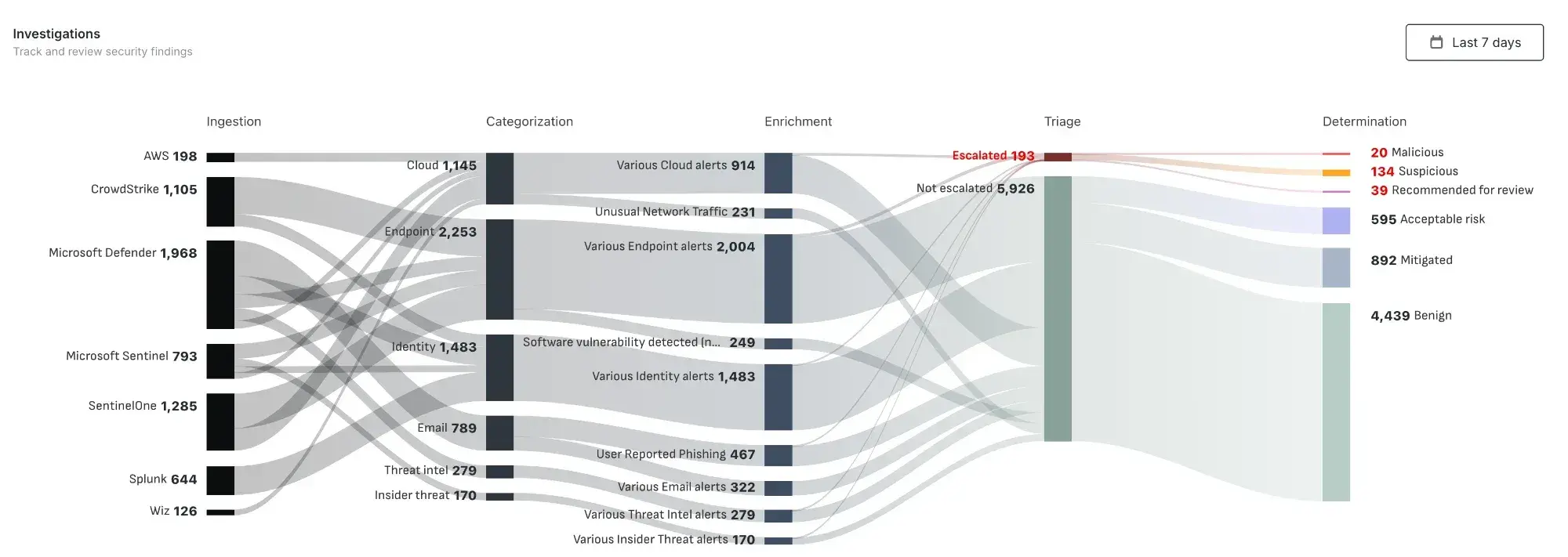
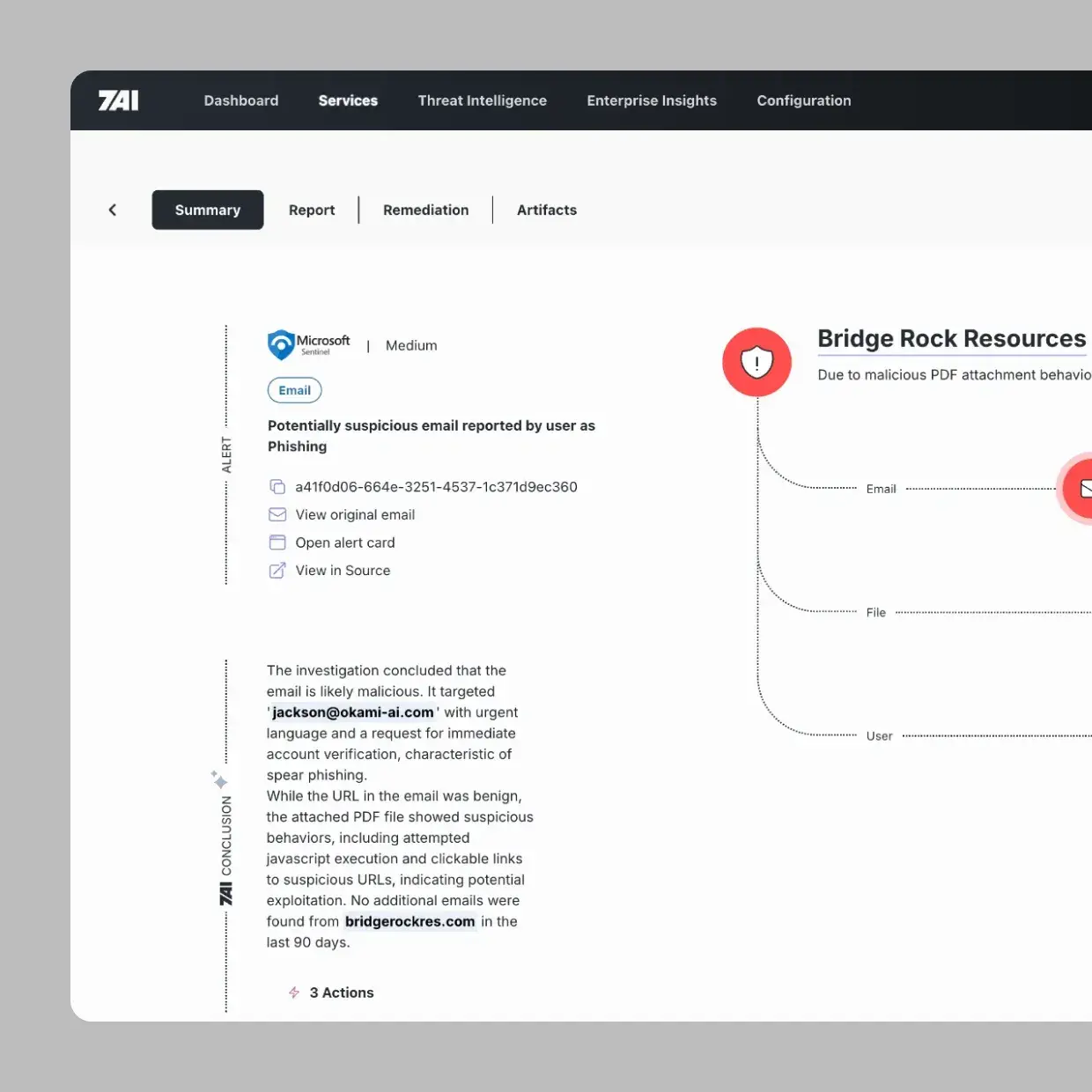
INVESTIGATIONS
AI agents that perform end-to-end security investigations at machine speed with expert-level reasoning..png)
What it Does
When an alert fires, swarming AI agents spring into action — enriching data, querying your environment, correlating across systems, and forming conclusions. What used to take analysts hours now happens in minutes.
- Autonomous enrichment & correlation
- Multi-system data gathering
- Conclusions with full evidence
- Complete investigation narrative
DETECTION
Intelligent alert processing that separates signal from noise before anything reaches your team.
.png)
What it Does
7AI ingests alerts from your security tools, applies AI-powered analysis, and delivers only what matters. Instead of drowning in thousands of alerts, your team sees actionable conclusions with full context and recommended actions.
- Multi-source alert ingestion
- AI-powered triage & enrichment
- Up to 95-99% false positive elimination
- Context-aware conclusions
RESPONSE
Flexible remediation options to take action based on investigation conclusions—not just predefined playbooks.
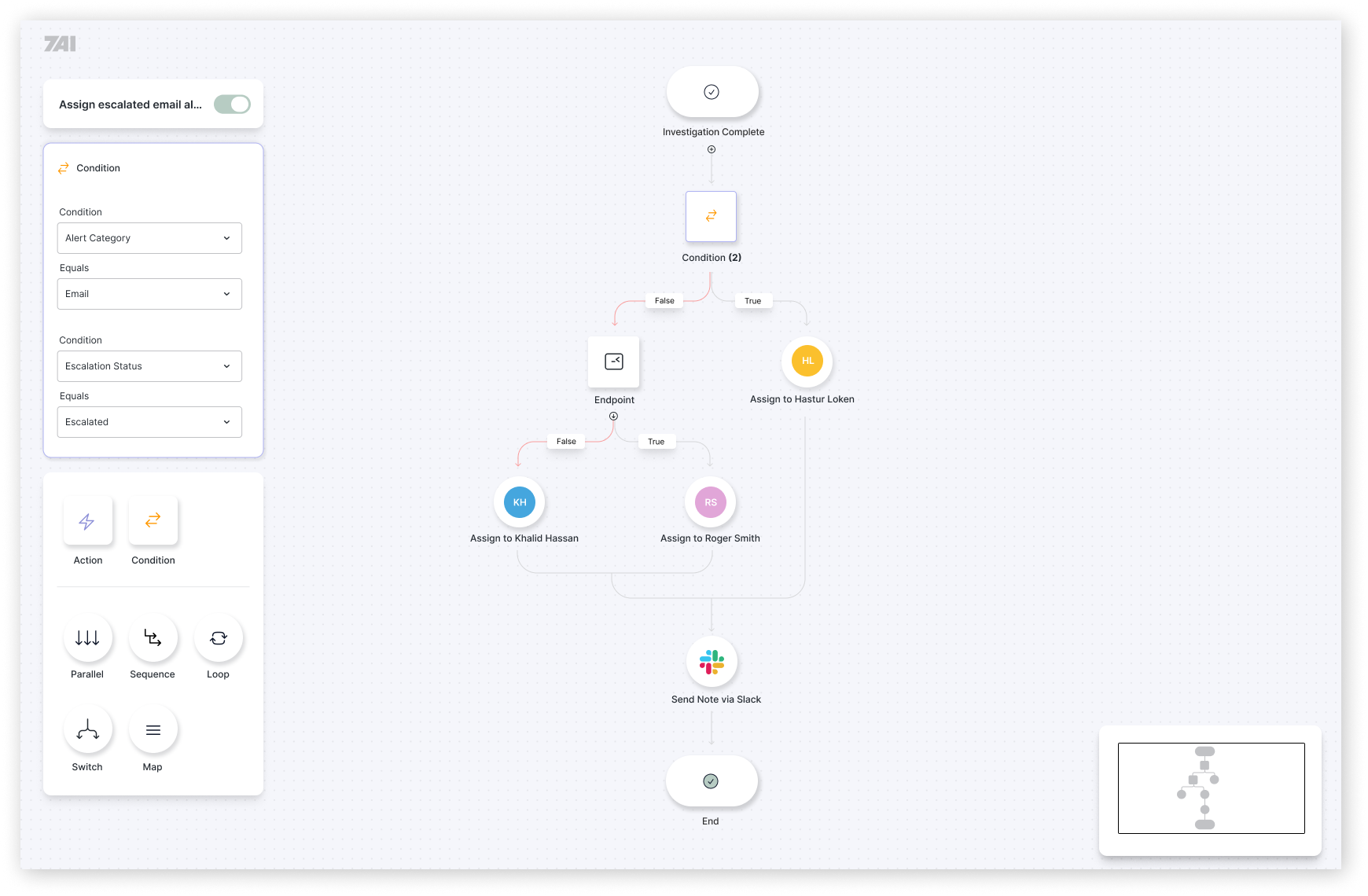
What it Does
When AI agents determine a threat is real, customers get flexible response options - from suggestions to automated actions. Isolate endpoints, disable accounts, block IPs, trigger custom workflows. Actions are tied to conclusions, not just pattern matching.
- Conclusion-driven actions
- Native integrations for containment
- Human-in-the-loop options
- Full audit trail
Workflow Builder
Build custom response workflows that match your organization's policies and procedures. Drag-and-drop logic, conditional branching, and integration with your existing tools—no coding required.
HUNTING
Proactive threat hunting powered by AI that lets analysts do the strategic work they were hired for.
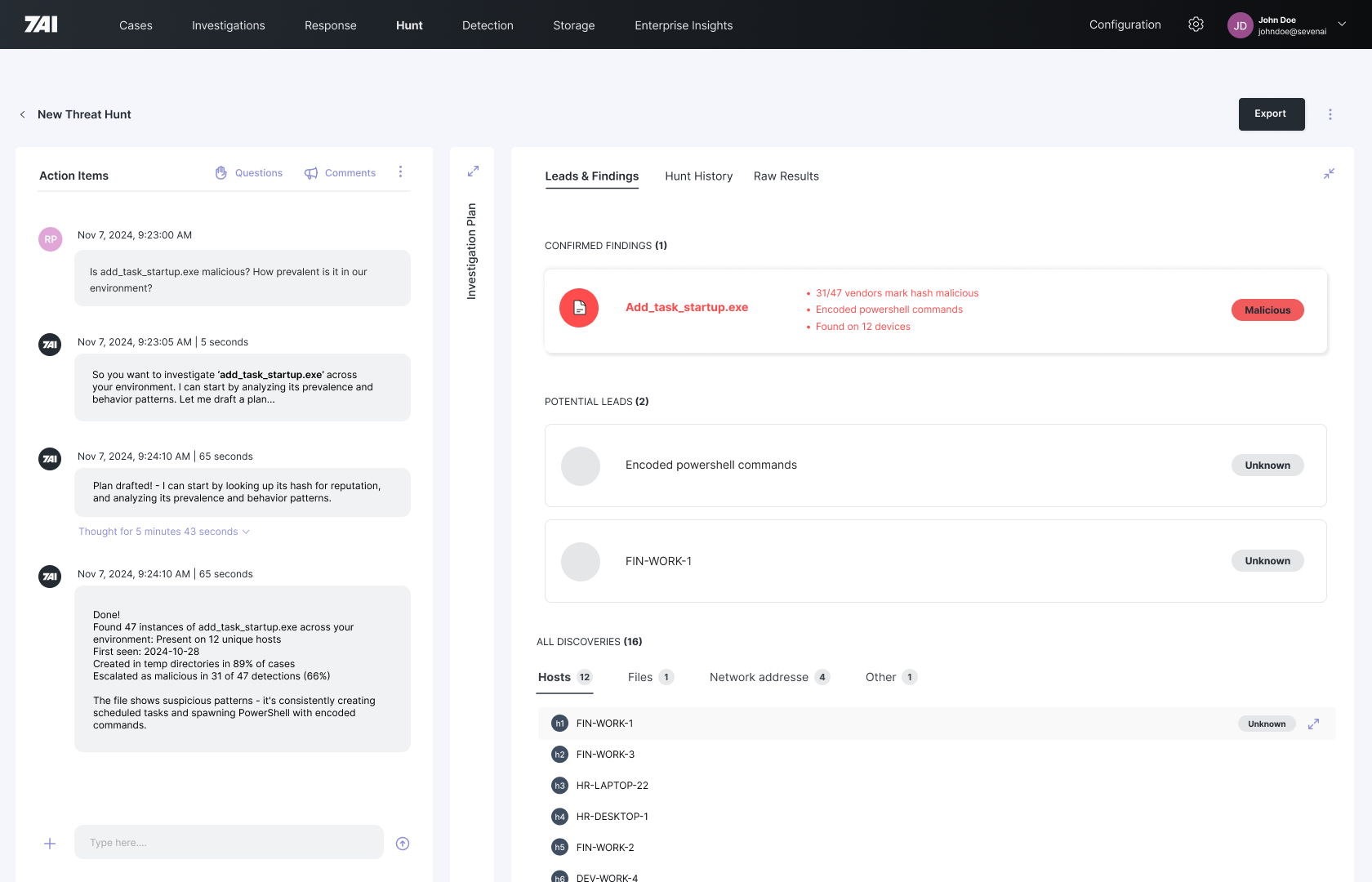
What it Does
With AI agents handling alert triage, your analysts are free to hunt. 7AI provides powerful threat hunting capabilities to uncover threats hiding in your environment.
- Cross-system threat correlation
- AI-powered hunt suggestions
- IOC extraction
- Historical analysis
ENTERPRISE INSIGHTS
AI agents that consider enterprise context dynamically at the time of investigation.
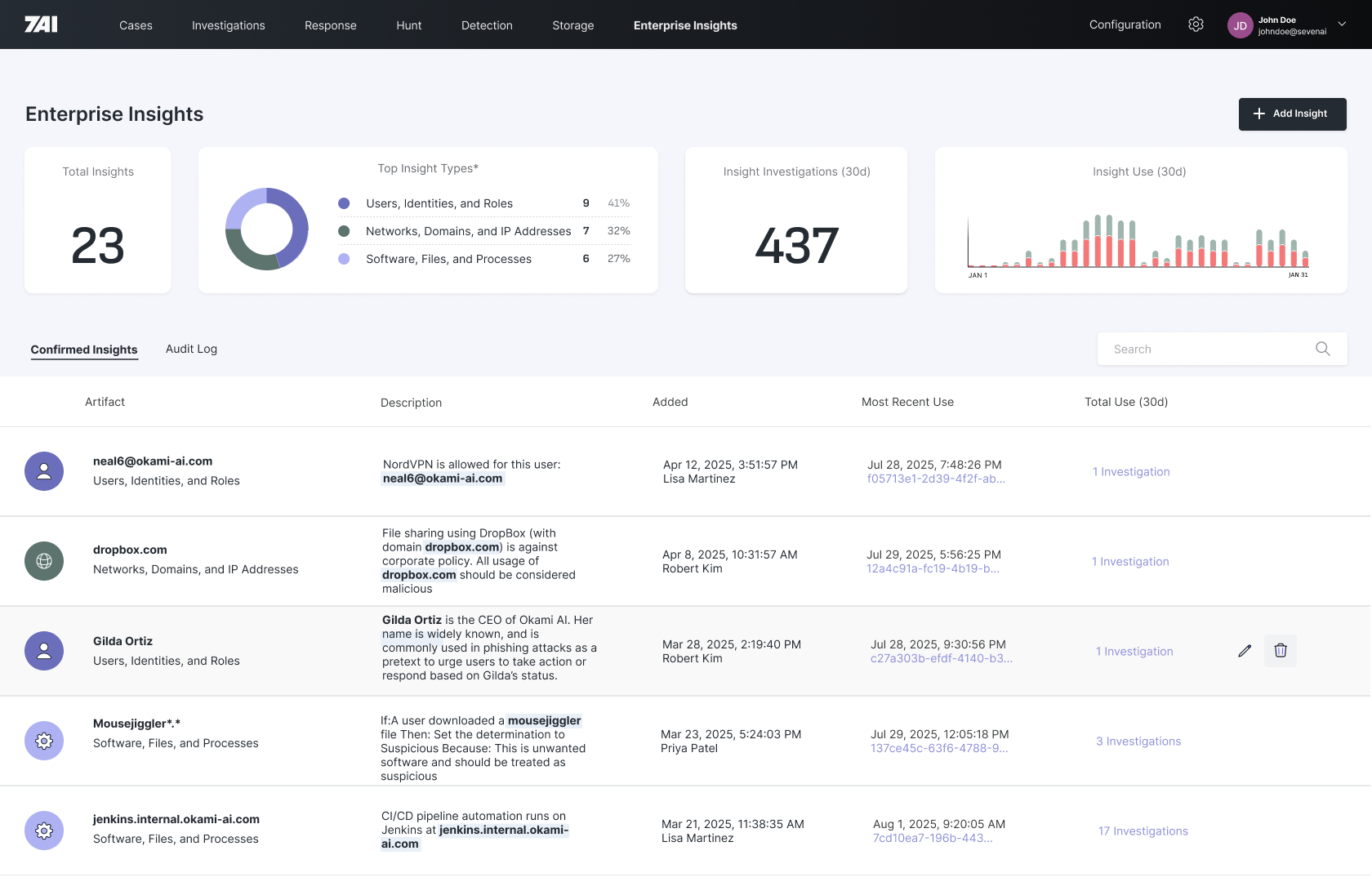
What it Does
7AI's Enterprise Insights captures organizational context to understand your unique policies, drastically reducing false positives by accounting for:
- Users and roles
- Allowed and disallowed software
- Nuanced conditions
- Customer and inferred findings
Agent Library
Purpose-Built Agents for Every Security Task
Each 7AI agent is an expert at specific security tasks, continuously expanding to cover new use cases and threat vectors.
-
Endpoint
Device Alert History and Correlation Agent
Surfaces past alerts on a device and relates them to current activity to detect escalating risk.
-
Endpoint
Device Enrichment Agent
Provides contextual data on a device including OS, owner, last activity, and vulnerability exposure.
-
Endpoint
Device ID Agent
Resolves multiple device identifiers to a canonical entity to ensure accurate correlation across alert sources.
-
Endpoint
Device Investigation Agent
Investigates the device’s recent activity, active processes, and connections to determine compromise likelihood.
-
Endpoint
File Investigation Agent
Performs static and dynamic analysis of files, looking for known signatures, behaviors, and propagation patterns.
-
Endpoint
File Provenance Agent
Traces the origin and modification path of a file across systems to determine source, spread, and potential data exfiltration.
-
Endpoint
File Remediation Agent
Automates quarantine or deletion of files confirmed to be malicious, using native EDR and endpoint controls.
-
Endpoint
File Reputation Agent
Determines if files are malicious, suspicious, benign, or unknown.
-
Endpoint
IP and Device Correlation Agent
Correlates IP addresses with known devices, sessions, and user activity to track movement and exposure.
-
Endpoint
Process Command-Line Agent
Inspects and interprets command-line arguments used during process execution to identify known attack patterns or scripting misuse.
-
Endpoint
Process Investigation Agent
Analyzes process behavior, ancestry, and execution context to detect suspicious or unauthorized activity on endpoints.
-
Endpoint
Registry Investigation Agent
Interrogates Windows registry changes associated with alerts to detect persistence mechanisms or configuration tampering.
-
Endpoint
SentinelOne Lineage Agent
Retrieves and analyzes lineage data from SentinelOne to reconstruct the origin and propagation path of detected threats.
-
Endpoint
Splunk Mission Control Activity Agent
Queries recent activity within Splunk Mission Control to identify prior related incidents or alert patterns for context.
-
Endpoint
Storyline Agent
Compiles a timeline of events and entities associated with an alert, connecting dots across systems to produce a coherent incident narrative.
-
Endpoint
URL Investigation Agent
Expands and inspects URLs associated with alerts, checking for phishing indicators, downloads, redirects, and reputation.
-
Identity
Login Activity Analysis Agent
Inspects login behavior across endpoints and identity providers to identify brute force attempts or session hijacks.
-
Identity
Okta User Enrichment Agent
Fetches data from Okta about user identity, group memberships, device associations, and MFA status.
-
Identity
Privilege Grantor Behavior Agent
Identifies accounts that granted elevated privileges and assesses whether the action aligns with normal administrative behavior.
-
Identity
Technical User Activity Agent
Monitors behavior of service and administrative accounts for unusual access patterns or risky command execution.
-
Identity
User Activity Analysis Agent
Analyzes user activity trails to identify deviations from typical behavior and detect signs of credential misuse or insider threats.
-
Identity
User Alert History and Correlation Agent
Surfaces past alerts tied to the same user and correlates with the current incident to detect patterns of compromise.
-
Identity
User Behavior Investigation Agent
Investigates a user's behavioral fingerprint to highlight anomalies in login, device usage, and data access patterns.
-
Identity
User Enrichment Agent
Enriches user entities with organizational role, authentication context, and recent access behavior for deeper investigation.
-
Identity
User Identity Enrichment Agent
Provides a consolidated identity view of a user across identity providers and activity sources to support correlation.
-
Identity
User Login History Agent
Compiles login events for a user across systems to flag geographic anomalies, impossible travel, or access outside work hours.
-
Identity
Windows User Enrichment Agent
Pulls contextual data from Windows environments about a given user, including group memberships and recent sessions.
-
Cloud
AWS Activity Analysis Agent
Surfaces AWS account-level activity anomalies by profiling user and service actions against baseline behaviors.
-
Cloud
AWS ELB Analysis Agent
Assesses configuration and access logs of AWS Elastic Load Balancers to detect misrouting, DDoS patterns, or privilege misuse.
-
Cloud
AWS Resource Enrichment Agent
Aggregates configuration and metadata from AWS resources to assess security posture and ownership.
-
Cloud
Azure Recent Activity Agent
Surfaces recent activity in Azure environments, identifying anomalous actions across users, service principals, and roles.
-
Cloud
Query Agent
Fetches and compiles data from multiple systems in response to investigative prompts, enabling deeper context generation.
-
Cloud
S3 Bucket Activity Analysis Agent
Tracks activity within S3 buckets to detect unusual access, modifications, or bulk downloads.
-
Cloud
S3 Bucket Enrichment Agent
Enriches AWS S3 bucket info with metadata including permissions, access logs, and exposure risk for security review.
-
Email
Email Content Agent
Performs semantic analysis on email body and subject for phishing indicators, urgency cues, or social engineering.
-
Email
Email DLP Content Agent
Evaluates email content against DLP policies to detect potential exfiltration or inappropriate data handling.
-
Email
Email Recipient Agent
Analyzes patterns of email recipients to detect potential misuse of distribution groups or anomalous communication.
-
Email
Email Sender Analysis Agent
Examines sender metadata and authentication to detect spoofing, typosquatting, or domain abuse.
-
Email
Retrieve Original Email Agent
Fetches the full raw email from the mail server for analysis of headers, links, attachments, and content.
-
Network
Distance Between IPs Agent
Calculates network and geographic proximity between IP addresses to evaluate possible lateral movement or coordinated attacker behavior.
-
Network
Domain Agent
Investigates and enriches domain-related observables, identifying reputation, WHOIS data, hosting details, and relationships to known threat infrastructure.
-
Network
External IP Investigation Agent
Performs enrichment and threat assessment for external IPs, correlating with threat intel feeds and identifying risky infrastructure.
-
Network
Internal IP Investigation Agent
Correlates internal IPs with associated assets and users, tracking movement across the environment for threat triage and attribution.
-
Network
IP Enrichment Agent
Aggregates geolocation, ASN, blacklist, and threat intel data for any observed IP address to aid in contextual alert triage.
-
Network
Network Investigation Agent
Evaluates network traffic metadata to uncover anomalies in volume, direction, and communication patterns tied to alerts.
-
Endpoint
Device Alert History and Correlation Agent
Surfaces past alerts on a device and relates them to current activity to detect escalating risk.
-
Endpoint
Device Enrichment Agent
Provides contextual data on a device including OS, owner, last activity, and vulnerability exposure.
-
Endpoint
Device ID Agent
Resolves multiple device identifiers to a canonical entity to ensure accurate correlation across alert sources.
-
Endpoint
Device Investigation Agent
Investigates the device’s recent activity, active processes, and connections to determine compromise likelihood.
-
Endpoint
File Investigation Agent
Performs static and dynamic analysis of files, looking for known signatures, behaviors, and propagation patterns.
-
Endpoint
File Provenance Agent
Traces the origin and modification path of a file across systems to determine source, spread, and potential data exfiltration.
-
Endpoint
File Remediation Agent
Automates quarantine or deletion of files confirmed to be malicious, using native EDR and endpoint controls.
-
Endpoint
File Reputation Agent
Determines if files are malicious, suspicious, benign, or unknown.
-
Endpoint
IP and Device Correlation Agent
Correlates IP addresses with known devices, sessions, and user activity to track movement and exposure.
-
Endpoint
Process Command-Line Agent
Inspects and interprets command-line arguments used during process execution to identify known attack patterns or scripting misuse.
-
Endpoint
Process Investigation Agent
Analyzes process behavior, ancestry, and execution context to detect suspicious or unauthorized activity on endpoints.
-
Endpoint
Registry Investigation Agent
Interrogates Windows registry changes associated with alerts to detect persistence mechanisms or configuration tampering.
-
Endpoint
SentinelOne Lineage Agent
Retrieves and analyzes lineage data from SentinelOne to reconstruct the origin and propagation path of detected threats.
-
Endpoint
Splunk Mission Control Activity Agent
Queries recent activity within Splunk Mission Control to identify prior related incidents or alert patterns for context.
-
Endpoint
Storyline Agent
Compiles a timeline of events and entities associated with an alert, connecting dots across systems to produce a coherent incident narrative.
-
Endpoint
URL Investigation Agent
Expands and inspects URLs associated with alerts, checking for phishing indicators, downloads, redirects, and reputation.
-
Identity
Login Activity Analysis Agent
Inspects login behavior across endpoints and identity providers to identify brute force attempts or session hijacks.
-
Identity
Okta User Enrichment Agent
Fetches data from Okta about user identity, group memberships, device associations, and MFA status.
-
Identity
Privilege Grantor Behavior Agent
Identifies accounts that granted elevated privileges and assesses whether the action aligns with normal administrative behavior.
-
Identity
Technical User Activity Agent
Monitors behavior of service and administrative accounts for unusual access patterns or risky command execution.
-
Identity
User Activity Analysis Agent
Analyzes user activity trails to identify deviations from typical behavior and detect signs of credential misuse or insider threats.
-
Identity
User Alert History and Correlation Agent
Surfaces past alerts tied to the same user and correlates with the current incident to detect patterns of compromise.
-
Identity
User Behavior Investigation Agent
Investigates a user's behavioral fingerprint to highlight anomalies in login, device usage, and data access patterns.
-
Identity
User Enrichment Agent
Enriches user entities with organizational role, authentication context, and recent access behavior for deeper investigation.
-
Identity
User Identity Enrichment Agent
Provides a consolidated identity view of a user across identity providers and activity sources to support correlation.
-
Identity
User Login History Agent
Compiles login events for a user across systems to flag geographic anomalies, impossible travel, or access outside work hours.
-
Identity
Windows User Enrichment Agent
Pulls contextual data from Windows environments about a given user, including group memberships and recent sessions.
-
Cloud
AWS Activity Analysis Agent
Surfaces AWS account-level activity anomalies by profiling user and service actions against baseline behaviors.
-
Cloud
AWS ELB Analysis Agent
Assesses configuration and access logs of AWS Elastic Load Balancers to detect misrouting, DDoS patterns, or privilege misuse.
-
Cloud
AWS Resource Enrichment Agent
Aggregates configuration and metadata from AWS resources to assess security posture and ownership.
-
Cloud
Azure Recent Activity Agent
Surfaces recent activity in Azure environments, identifying anomalous actions across users, service principals, and roles.
-
Cloud
Query Agent
Fetches and compiles data from multiple systems in response to investigative prompts, enabling deeper context generation.
-
Cloud
S3 Bucket Activity Analysis Agent
Tracks activity within S3 buckets to detect unusual access, modifications, or bulk downloads.
-
Cloud
S3 Bucket Enrichment Agent
Enriches AWS S3 bucket info with metadata including permissions, access logs, and exposure risk for security review.
-
Email
Email Content Agent
Performs semantic analysis on email body and subject for phishing indicators, urgency cues, or social engineering.
-
Email
Email DLP Content Agent
Evaluates email content against DLP policies to detect potential exfiltration or inappropriate data handling.
-
Email
Email Recipient Agent
Analyzes patterns of email recipients to detect potential misuse of distribution groups or anomalous communication.
-
Email
Email Sender Analysis Agent
Examines sender metadata and authentication to detect spoofing, typosquatting, or domain abuse.
-
Email
Retrieve Original Email Agent
Fetches the full raw email from the mail server for analysis of headers, links, attachments, and content.
-
Network
Distance Between IPs Agent
Calculates network and geographic proximity between IP addresses to evaluate possible lateral movement or coordinated attacker behavior.
-
Network
Domain Agent
Investigates and enriches domain-related observables, identifying reputation, WHOIS data, hosting details, and relationships to known threat infrastructure.
-
Network
External IP Investigation Agent
Performs enrichment and threat assessment for external IPs, correlating with threat intel feeds and identifying risky infrastructure.
-
Network
Internal IP Investigation Agent
Correlates internal IPs with associated assets and users, tracking movement across the environment for threat triage and attribution.
-
Network
IP Enrichment Agent
Aggregates geolocation, ASN, blacklist, and threat intel data for any observed IP address to aid in contextual alert triage.
-
Network
Network Investigation Agent
Evaluates network traffic metadata to uncover anomalies in volume, direction, and communication patterns tied to alerts.
HIGHLIGHTED CONNECTORS
The 7AI Agentic Security Platform connects to IT and Security tools, enabling agents to enrich, investigate, and form conclusions. The following is a highlighted list of API-based connectors available today.

Abnormal

AbuseIPDB

Alienvault OSSIM
Amazon Cloud Trail

Amazon GuardDuty

Anthropic

AWS

Censys

Chronicle

Cisco Secure

Confluence

Cortex

Crowdstrike

Databricks

Datadog

DNSlytics

Elastic

Gmail

Google Cloud

Google SecOps

Google Workspace

Hybrid Analysis

IBM Radar

IPinfo

Jira


Microsoft 365
.png)
Microsoft Azure

Microsoft Entra

Microsoft Excel

Office 365

Microsoft Sentinel

Microsoft Teams

Mimecast

NVD

Okta

PagerDuty

Panther

PhishTank

Proofpoint

Qualys

Reversing Labs

Secureworks

Sentinel One

Servicenow

Slack

Snowflake

Splunk

Spur

Stellar Cyber

Sumo Logic

Tenable

URL haus

Urlscan.io

Virus Total

Wiz
See the Platform in Action
Schedule a conversation with our team. We'll learn about your environment, understand what you're trying to solve, and show you exactly how 7AI transforms security operations.